Security experts have found over 90 Android apps on Google Play, the official download store for Android phones, that were infected with malware. Android users have installed these dangerous apps over 5.5 million times on Android devices.
The banking Trojan “Anatsa” alias “Teabot” plays an inglorious, important role in this. Anatsa attacks over 650 apps from financial institutions. These are banks from the UK, Europe, the USA and Asia.
Find the best antivirus apps for Android to protect your device
The Trojan attempts to steal access data for online banking and use it to carry out fraudulent banking transactions. Anatsa hides in various apps that pretend to be productivity tools. In February 2024, Anatsa used this disguise to achieve at least 150,000 infections via Google Play.
Now, in May 2024, Anatsa managed to break into Google Play again, as you can read in this document from Zscaler. Cyber crooks spread the banking Trojan via the harmless and useful-sounding apps “PDF Reader & File Manager” and “QR Reader & File Manager”.
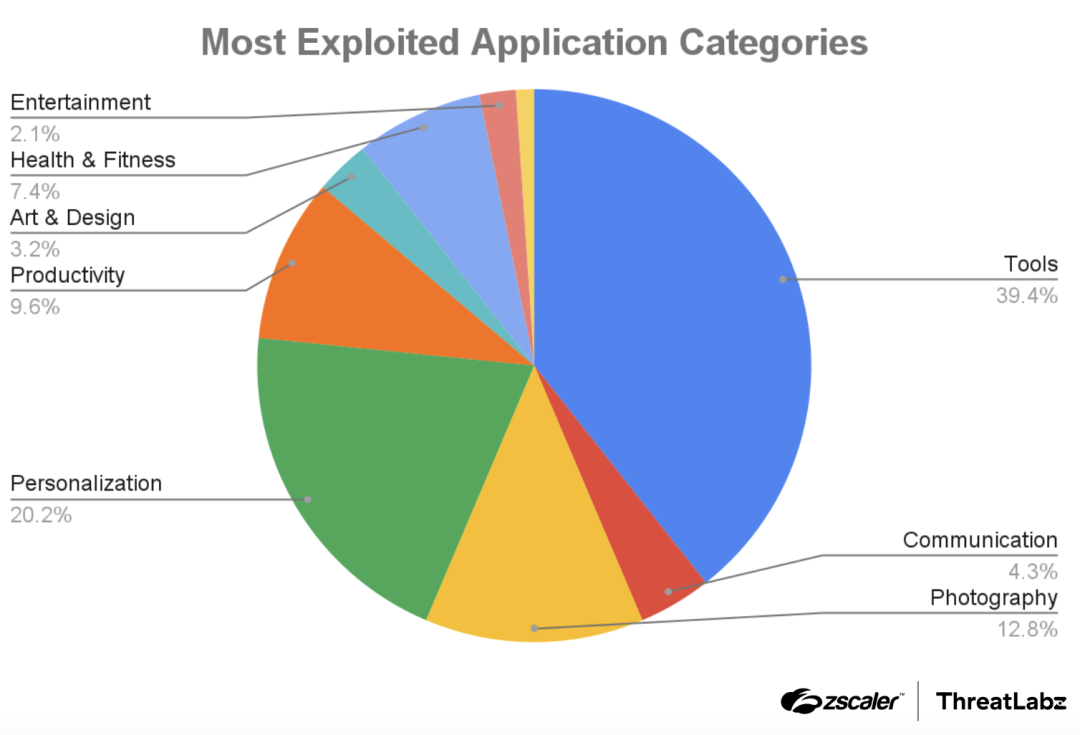
At the time the security company Zscaler carried out its investigation, users had installed these two infected apps around 70,000 times on their devices. The report highlights ‘Tools’ as the most popular category of apps to target. They make up almost 40% with ‘personalization’ and ‘photography’ accounting for 20% and 13% respectively.
Zscaler
How does it happen?
Anatsa evades Google’s malware detection by loading its malicious components in several stages. First, the dropper app retrieves the configuration and important strings from the hackers’ command-and-control servers. Then the app downloads the DEX file with the malicious dropper code and activates it on the Android device.
The app then downloads the configuration file with the Anatsa payload URL. Finally, the DEX file retrieves and installs the actual malware as an APK file, thereby completing the infection process. The DEX file also checks that the malware is not executed in sandboxes or within emulations, where it would remain ineffective.
Once Anatsa is running on the newly infected Android, it uploads the bot configuration and app scan results to the servers and then downloads the targeted “injections” that match the location and profile of the victim device.
As already mentioned, Anatsa is just one type of malware that is currently particularly active on Google Play. In total, the security experts found over 90 infected apps (the names of which were not published by the security researchers) that Android users have installed over 5.5 million times.
These apps disguise themselves as tools, personalisation apps, photography utilities, productivity apps and health and fitness apps. Google has now removed the infected apps from Google Play.
How to protect yourself
As a general rule, you should only download Android apps from Google Play and avoid other download offers – even if the hackers were able to trick Google’s security mechanisms in the case described here.
Read the permissions that an app requires on your device before every download. Critically question whether these authorisations make sense or whether they go too far.
Also be extremely wary of any phone calls you might receive when using apps, particularly a banking app while making a payment or transaction.
You should also install antivirus on your Android device.
This article originally appeared on our sister publication PC-WELT and was translated and adapted from German.


